Fun & effective CEH practice test tool to pass with flying colors
All-in-one platform with everything you need to ace the CEH on your first attempt
Clear and Thorough Learning Path
Proven CEH 3-step Practice Formula
After our 100,000+ users' success stories, we developed a 3-step strategy to provide you with the most precise and in-depth learning path while minimizing your prep time.CEH Diagnostic Test
First, take this short test and get your detailed report showing your strong and weak areas. Save your time by concentrating on what is in demand.Learning
With quick, bite-sized learning techniques and a detailed study guide for each CEH section, you can really strengthen your weaknesses (from step 1) and boost your scores.CEH Full Test
The last step for your preparation is taking our full CEH practice tests and seeing how far you've come since the beginning. Repeat the 3-step formula until you are satisfied with your results!Ready to start?
Thousands of CEH users already accomplished their goals.NOW it’s your turn!

What You Get
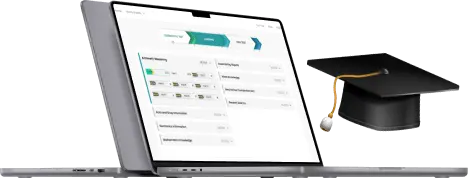
All-in-one platform
A complete CEH Prep Platform, including a diagnostic test, detailed study guides for all topics, practice questions with step-by-step explanations, and various full simulator tests.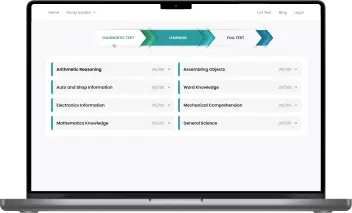
Questions nearly identical to those in the real CEH test
All questions are categorized into the specific sections as on the real CEH: Same format & same difficulty!
Best for the busy
Easily & quickly grasp all the knowledge with our unique learning technique. And you can learn anytime, anywhere on any devices, even with a few free minutes.
Practice while having fun
Learn and play! Complete round-by-round to reach your daily achievement and make progress on your learning journey!Featured on















What our users are saying
Over 50,000 aspiring American candidates use CEH monthlyCEH Certification: The Most Comprehensive Guide in 2024
The Certified Ethical Hacker (CEH) certification is for security professionals who want to demonstrate that they can evaluate weaknesses in target systems using techniques commonly associated with hackers to help employers or clients identify vulnerabilities. CEH (also known as C|EH) is the most well-known certification offered by the International Council of Electronic Commerce Consultants, often known as EC-Council.
Over 237,000 security professionals from private and public corporation have been certified by the EC-Council. They boast members working at IBM, the US Army, the FBI, Microsoft, and the United Nations.
In this article, we provide the most comprehensive guide to getting the CEH certification in 2024.
What Is The Certified Ethical Hacker Certification?
The EC-Certified Council's Ethical Hacker (CEH) certification validates your ability to bypass an organization's security defenses by getting access to their databases, applications, and other critical data through gaps in the security construct.
It assesses your ability to find vulnerabilities that a malicious attacker could exploit. A CEH certification equips you with an in-depth understanding of hacking tools, evolving attack vectors, and preventative countermeasures, allowing you to match the techniques and creativity of a black hat hacker.
Before evaluating an asset for vulnerabilities, certified ethical hackers obtain permission from the asset owner and ensure that the results are kept private. Passing the CEH (ANSI) exam is the first stage in becoming a certified ethical hacker. After that, you can choose to take the CEH practical exam, which is a six-hour practical exam. A CEH Master is a professional who has obtained CEH certification and passed the CEH practical.
Is CEH a Good Certification?
The CEH is a globally recognized certification that has become the standard measure for many corporations when hiring pentesters and other cyber security professionals. With that in mind, as well as the extensive material covered on the exam, pursuing the CEH is worthwhile.
What Jobs Can I Get With CEH Certification?
Network security specialists are required in a variety of roles today to secure the safety of a company's data and operations. People having a CEH certification can work in the following network security roles:
|
Job |
National Average Salary |
|
Website administrator |
USD $43,342 per year |
|
IT security specialist |
USD $66,099 per year |
|
Information security analyst |
USD $94,127 per year |
|
Cybersecurity analyst |
USD $95,029 per year |
|
IT auditor |
USD $95,568 per year |
|
Network engineer |
USD $96,088 per year |
|
Chief information officer (CIO) |
USD $125,900 per year |
|
Software architect |
USD $135,377 per year |
The CEH's acceptance by the industry has reinforced the idea that ethical hacking is not just a useful skill but also a respected profession. Acceptance has provided respectability to a subset of computer and network skills that were previously only pursued by malicious actors.
CEH Certification Requirements
You have two options when it comes to the CEH certification exam eligibility requirements.
To start, you can take an official EC-Council training at an accredited training center, an approved academic institution, or on the iClass platform. You can take the EC-Council certification exam without going through the application process in this case.
As a condition for the second option for CEH certification eligibility, you must have at least two years of experience in the information security domain. You can submit your application along with a $100 fee if you have relevant experience (non-refundable).
You must put your manager's details on the application form, as they will act as verifiers during the application process. Once the verifier responds to the EC-request Council for information, the application usually takes five to ten working days.
Our CEH Application features
Free Practice Questions: 500+ free CEH practice questions with detailed explanations are available for all of the required skills. All you need to pass your recruitment test is available here.
CEH Practice Tests Based On Real Tests: Same number of questions, same time limits, same structure. The exam simulators let you familiarize yourself with the test format and get totally ready for the real one.
No Sign-Up Or Login Required: All of your progress is saved without an account, even if you close your browser. But login can sync your data between web and mobile applications.
Gamification: The learning process will be divided into small milestones. Let’s make your studying exciting as if you were in some interesting games.
Personal Study Plan: Just enter your CEH test date, and a study plan will be set up for you. A clear schedule will surely exceed your expectation and get you the best preparation for the reading shot.
3 Interesting Test Modes: 3 different test modes with increased difficulty levels let you experience the CEH practice test in various ways.
Dark Mode: Experience a dark theme that is more friendly to your eyes, and get a whole new and marvelous experience.
No Internet Required: Study on the go conveniently without any Internet connection.
CEH Test Bank: 3 features: Weak/ Medium/ Strong questions help you clearly determine which area you should pay more attention to.
CEH Exam Format
How Many Questions on CEH Exam?
The CEH exam consists of 125 multiple-choice questions. The CEH exam will take 4 hours to complete. As all of the questions are multiple-choice, test takers rarely run out of time. Many candidates report that this test took them only two to three hours to complete.
How Long is The CEH Exam?
The CEH exam has a four-hour time limit to complete the 125 questions.
What is the CEH Passing Score?
The CEH exam passing score is interesting in that no specific passing score or percentage exists. According to EC-Council, a common misconception is that you must properly answer 70% of the questions to pass. The actual percentage varies, depending on the difficulty of the questions and the input offered by subject-matter experts who set the pass/fail cut score.
Cut scores range from 60% to 85% based on which question bank is used, are based on the knowledge and skills required to demonstrate competence in the subject areas provided to a candidate.
Certified Ethical Hacker exam pass rate varies depending on the candidate's training and experience, however, Infosec's Ethical Hacking boot camp has a 93% exam pass rate.
What Are CEH Subjects?
125 questions are divided into nine domains in the CEH credential exams 312-50 (ECC EXAM) and 312-50 (VUE).
Information Security and Ethical Hacking Overview (6%)
- Information Security Overview
- Cyber Kill Chain Concepts
- Hacking Concepts
- Ethical Hacking Concepts
- Information Security Controls
- Information Security Laws and Standards
Reconnaissance Techniques (21%)
Footprinting and Reconnaissance
- Footprinting Concepts
- Footprinting Methodology
- Footprinting through Search Engines
- Footprinting through Web Services
- Footprinting through Social Networking Sites
- Website Footprinting
- Email Footprinting
- Whois Footprinting
- DNS Footprinting
- Network Footprinting
- Footprinting through Social Engineering
- Footprinting Tools
- Footprinting Countermeasures
Scanning Networks
- Network Scanning Concepts
- Scanning Tools
- Host Discovery
- Port and Service Discovery
- OS Discovery (Banner Grabbing/OS Fingerprinting)
- Scanning Beyond IDS and Firewall
- Draw Network Diagrams
Enumeration
- Enumeration Concepts
- NetBIOS Enumeration
- SNMP Enumeration
- LDAP Enumeration
- NTP and NFS Enumeration
- SMTP and DNS Enumeration
- Other Enumeration Techniques (RPC, IPsec, Telnet, VoIP, Unix/Linux, SMB, TFTP, FTP, IPv6, and BGP enumeration)
- Enumeration Countermeasures
System Hacking Phases and Attack Techniques (17%)
Vulnerability Analysis
- Vulnerability Assessment Concepts
- Vulnerability Classification and Assessment Types
- Vulnerability Assessment Solutions and Tools
- Vulnerability Assessment Reports
System Hacking
- System Hacking Concepts
- Gaining Access
- Cracking Passwords
- Vulnerability Exploitation
- Escalating Privileges
- Maintaining Access
- Executing Applications
- Hiding Files
- Clearing Logs
Malware Threats
- Malware Concepts
- APT Concepts
- Trojan Concepts
- Virus and Worm Concepts
- File-less Malware Concepts
- Malware Analysis
- Malware Countermeasures
- Anti-Malware Software
Network and Perimeter Hacking (14%)
Sniffing
- Sniffing Concepts
- Sniffing Technique: MAC Attacks
- Sniffing Technique: DHCP Attacks
- Sniffing Technique: ARP Poisoning
- Sniffing Technique: Spoofing Attacks
- Sniffing Technique: DNS Poisoning
- Sniffing Tools
- Sniffing Countermeasures
- Sniffing Detection Techniques
Social Engineering
- Social Engineering Concepts
- Social Engineering Techniques
- Insider Threats
- Impersonation on Social
- Networking Sites
- Identity Theft
- Social Engineering Countermeasures
Denial-of-Service
- DoS/DDoS Concepts
- DoS/DDoS Attack Techniques
- Botnets
- DDoS
- Case Study
- DoS/DDoS Attack Tools
- DoS/DDoS Countermeasures
- DoS/DDoS Protection Tools
Session Hijacking
- Session Hijacking Concepts
- Application Level Session Hijacking
- Network Level Session Hijacking
- Session Hijacking Tools
- Session Hijacking Countermeasures
Evading IDS, Firewalls, and Honeypots
- IDS, IPS, Firewall, and Honeypot Concepts
- IDS, IPS, Firewall, and Honeypot Solutions
- Evading IDS
- Evading Firewalls
- IDS/Firewall Evading Tools
- Detecting Honeypots
- IDS/Firewall Evasion Countermeasures
Web Application Hacking (16%)
Hacking Web Servers
- Web Server Concepts
- Web Server Attacks
- Web Server Attack Methodology
- Web Server Attack Tools
- Web Server Countermeasures
- Patch Management
- Web Server Security Tools
Hacking Web Applications
- Web App Concepts
- Web App Threats
- Web App Hacking Methodology
- Footprint Web Infrastructure
- Analyze Web Applications
- Bypass Client-Side Controls
- Attack Authentication Mechanism
- Attack Authorization Schemes
- Attack Access Controls
- Attack Session Management Mechanism
- Perform Injection Attacks
- Attack Application Logic Flaws
- Attack Shared Environments
- Attack Database Connectivity
- Attack Web App Client
- Attack Web Services
- Web API, Webhooks and Web Shell
- Web App Security
SQL Injection
- SQL Injection Concepts
- Types of SQL Injection
- SQL Injection Methodology
- SQL Injection Tools
- Evasion Techniques
- SQL Injection Countermeasures
Wireless Network Hacking (6%)
- Wireless Concepts
- Wireless Encryption
- Wireless Threats
- Wireless Hacking Methodology
- Wireless Hacking Tools
- Bluetooth Hacking
- Wireless Countermeasures
- Wireless Security Tools
Mobile Platform, IoT, and OT Hacking (8%)
Hacking Mobile Platforms
- Mobile Platform Attack Vectors
- Hacking Android OS
- Hacking iOS
- Mobile Device Management
- Mobile Security Guidelines and Tools
IoT and OT Hacking
- IoT Concepts
- IoT Attacks
- IoT Hacking Methodology
- IoT Hacking Tools
- IoT Countermeasures
- OT Concepts
- OT Attacks
- OT Hacking Methodology
- OT Hacking Tools
- OT Countermeasures
Cloud Computing (6%)
- Cloud Computing Concepts
- Container Technology
- Serverless Computing
- Cloud Computing Threats
- Cloud Hacking
- Cloud Security
Cryptography (6%)
- Cryptography Concepts
- Encryption Algorithms
- Cryptography Tools
- Public Key Infrastructure (PKI)
- Email Encryption
- Disk Encryption
- Cryptanalysis
- Countermeasures
How Much Does It Cost For CEH?
In contrast to other IT certifications, you must apply to take the CEH. EC-Council would be interested to see if you have attended official CEH training or have at least 2 years of security experience throughout the application procedure. Moreover, there is a fee associated with each stage.
CEH with Training: Average USD $4,000
The following are the charges for becoming a Certified Ethical Hacker through EC-Council official training:
- Certified Ethical Hacker training: USD $850 to USD $2,999
- Certified Ethical Hacker examination price: USD $1,199
- Certified Ethical Hacker remote proctoring: USD $100
CEH with Self-Paced Training: Average USD $2,550
It is the base price for self-paced learning options and CEH assessments:
- Certified Ethical Hacker self-paced training (six months): USD $250 to USD $600
- Certified Ethical Hacker examination cost: USD $1,199
- Certified Ethical Hacker remote proctoring: USD $100
- Certified Ethical Hacker application cost: USD $100
The overall CEH Certification Cost is USD $1,699 to USD $2,049
CEH Exam Retake Cost
Exam center voucher to retake the CEH exam at a CEH retest voucher that cost USD $499.
- If a candidate fails to pass the exam on the first attempt, no cooling or waiting period is required before taking the exam again (1st retake).
- If a candidate fails on the second attempt (1st retake), they must wait 14 days before taking the exam again (2nd retake).
- If a candidate fails the third attempt (2nd retake), a 14-day waiting period is required before attempting the exam for the fourth time (3rd retake).
- If a candidate fails the fourth attempt (3rd retake), he or she must wait 14 days before taking the exam again (4th retake).
- A candidate may not take an exam more than five times in a 12-month (1 year) period, and a 12-month (1 year) waiting period will be imposed before attempting the exam for the sixth time (5th retake).
- Candidates who pass the exam are not entitled to take the same version of the exam again.
Candidates who fail the exam for the third time (2nd retake) are strongly encouraged to attend official hands-on training that addresses the certification objectives. This regulation does not apply to the LPT (Master) Exam.
Candidates who attempt the exam without following EC-Council's retake policy, as stated above, risk having their certification rights revoked.
How To Get CEH Certification
- Get a related bachelor's degree
A bachelor's degree in a field related to ethical hacking, such as computer science or cybersecurity, is beneficial to start your career. While some coding jobs do not require a degree, many network security positions do require prior experience with networks, programming, or comparable systems to guarantee that employees understand their obligations and tasks. This means that having a bachelor's degree may make it easier for you to find a job in the security field and start your journey toward CEH certification.
- Gain experience
Once you have your degree, look for a job in network security to begin gaining useful experience before taking the CEH exam. Candidates must have two years of security experience before taking an exam, according to the EC-Council, which administers it. You can, however, bypass this requirement by enrolling in certified CEH training and exam courses and learning about ethical hacking and security from experienced instructors. This experience will help you prepare for the exam and provide you the skills you'll need to be a successful ethical hacker.
- Apply for the exam
There are other levels of CEH exams from which to select, but the first level requires an application to the EC Council, proof of previous experience, and payment of an application fee. The EC Council usually reviews applications for accuracy before responding to candidates within a few days. You can register for the CEH exam and finish your preparation after the EC Council approves your application.
- Pass the exam and receive certification
CEH exams typically last four hours and include a variety of questions divided into sections. To ensure that participants cannot simply share answers, each exam normally has many versions with different questions. The difficulty level of the questions on the specific test you take determines a passing score. When you pass the exam and receive your CEH certification, you may add it to your CV and use it to start your career as a certified ethical hacker.
How Long Is CEH Out For?
Applicants who pass the exam are certified for three years and must earn EC-Council Continued Education (ECE) credits during that period. To be re-accredited for the next three years, certified members will need to acquire 120 credits.
Applicants who pass the exam are certified for three years and must earn EC-Council Continued Education (ECE) credits during that period. To be re-accredited for the next three years, certified members will need to acquire 120 credits.
CEH Certification Validity Check
Should you need to check the validity of your code, your CEH certification number or request an exam voucher extension, just enter your information here or you can contact [email protected] and one of our customer service people would be pleased to assist you.
FAQs - CEH Certification
What is a Certified Ethical Hacker?
A skilled professional who understands and knows how to seek for weaknesses and vulnerabilities in target systems is known as a Certified Ethical Hacker. A CEH-certified individual uses the same skills and tools as a malicious hacker but in a legal and ethical manner.
How Many Questions on CEH Exam?
The CEH exam consists of 125 multiple-choice questions. The CEH exam will take four hours to complete. Since all of the questions are multiple-choice, test takers rarely run out of time. Many candidates report that this test took them only two to three hours to complete.
How Long is The CEH Exam?
The CEH exam has a four-hour time limit to complete the 125 questions.
What score do you need to pass CEH?
The International Council of E-Commerce Consultants (EC-Council) offers the Certified Ethical Hacker (CEH) exam, which is approved by the American National Standards Institute (ANSI). The exam is made up of 125 multiple choice questions which must be completed in four hours with a 70% passing score.
What are the eligibility requirements for CEH certification?
To be eligible for the CEH exam, a candidate must have at least two years of information security experience, submit a USD $100 non-refundable eligibility application fee, complete an eligibility application form, and receive formal approval from EC-Certification Council's Department.
Where can I take the CEH exam?
The CEH exam is available at Pearson VUE testing centers. It is a computer-based exam.
Is CEH hard to pass?
In fact, students typically find that they have enough time during the four-hour exam to answer all 125 questions and that with proper preparation, the exam is thorough but not overly difficult to pass. You'll need to pay close attention to each question and answer accordingly.
Is the CEH certification worth it?
The CEH is a well-known pen-testing certification that has a great combination of attainability The CEH is a well-known pen-testing certification with a high level of attainability and reputation. The CEH is a good first penetration testing certification since almost all other penetration testing certifications are either less widely known or more difficult to obtain.
How much does the CEH certification cost?
USD USD 1,199
CEH costs USD $1,199 (non-member) and this exam does not include performance-based questions.
How long does it take to get CEH certification?
The course will last nine (9) weeks if you follow our recommended schedule just after Live Online sessions.
Is CEH open book?
It is an open book exam, which means you are free to use all of the resources on your computer, access sites, and search the internet for information. There are, nevertheless, several important restrictions: The official CEH training materials are not accessible.
What happens if you fail the CEH exam?
If a candidate fails to pass an EC-Council exam, he or she can acquire an ECC Exam center voucher to retake the exam at a reduced cost. If a candidate fails to pass the exam on the first attempt, no cooling or waiting period is required before retaking the exam (1st retake).
Can I get a job after CEH?
CEH certification from EC-Council is the most popular and coveted certification. CEH-certified professionals are frequently employed in the following positions:
- Website administrator
- IT security specialist
- Information security analyst
- Cybersecurity analyst
- IT auditor
- Network engineer
- Chief information officer (CIO)
- Software architect
Can I take CEH without experience?
Unless the candidate attends official training, the CEH (ANSI) program requires the candidate to have two years of work experience in the Information Security area and be able to present proof of the same as confirmed through the application procedure.
Does CEH expire?
Your CEH certification is good for three years. To keep your certification, you must earn a total of 120 credits within the ECE cycle period of three years.
What is the current version of CEH exam?
The current version is the CEH V11, which, like previous versions, uses the EC-exam Council's code 312-50.
Conclusion
Because of the increasing demand for ethical hackers, whether as a member of a red team, a pentester, or a freelance offensive consultant, now is an excellent time to get into the field and earn the CEH certification to benefit from a high job placement and perhaps higher salary rates.
Don’t forget to take our free CISSP practice test to get familiarized with the format as well as the questions of the actual exam to strengthen your knowledge and skills, as a result, enhancing your chance to pass the CISSP exam with a high score on your first attempt. Good luck to you!






