CompTIA is attempting to include some of the CEH (Certified Ethical Hacker) requirements for basic command output recognition. In comparison to CEH, there’s not much difference, just a little. However, they want you to do some very introductory CEH work of interpreting tool output. The output of commands showing IP address assignment, ping, traceroute, and netstat must be interpreted. Because this doesn’t seem to be mentioned in CompTIA’s exam description, we will briefly explain commands to know for Security+.
Don’t forget to take our free CompTIA Security+ practice test to pass the exam with a flying score on the first try.
Commands to Know for Security+: IP Address Assignment
Linux
On Linux, the old involves the ifconfig command:
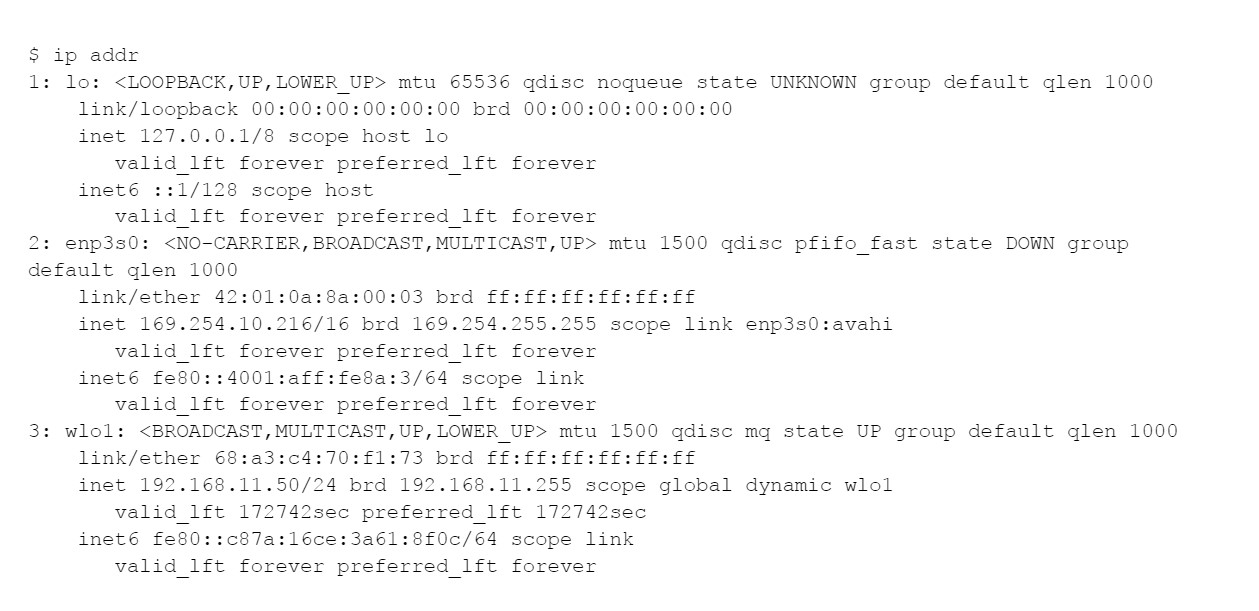
We can no longer rely on ifconfig; instead, the ip command is a new way:
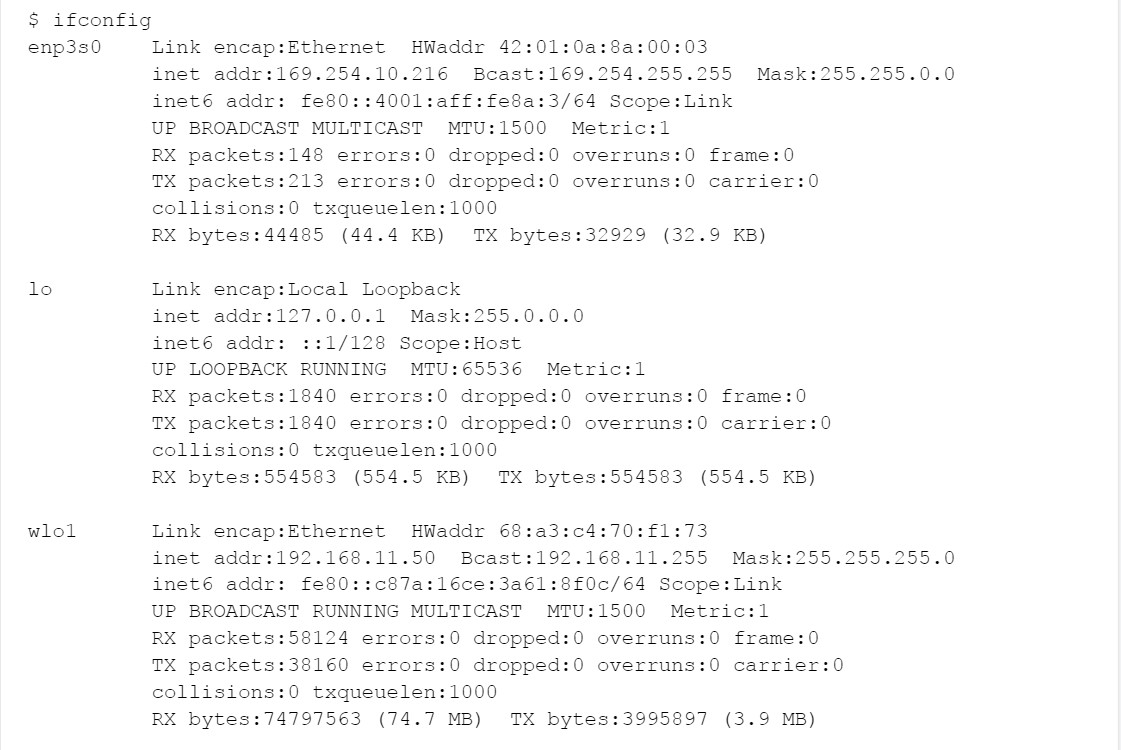
What do you need to know about the above for the Security+ exam?
IPv4 addresses are 32-bit strings, are represented as four base-10 numbers in the range 0-255, and are separated by dots. In the above, the software loopback or “localhost” interface lo gets, 127.0.0.1, the wired Ethernet interface enp3s0 gets 169.254.10.216, and the wireless interface wlo1 gets 192.168.11.50. It’s “lo” for loopback, “wl” for wireless, and “e” for Ethernet.
In particular, you should recognize the following:
Loopback or lo is assigned 127.0.0.1/8, which means that the first 8 bits or 127.*.*.* define the network. That is, communication is within this host only.
The wired Ethernet or enp3s0 was assigned 169.254.10.216/16, which means that 169.254.*.* is the network itself, 169.254.10.216 is this device in particular, and 169.254.*.* is the “AutoConf” address block. This assignment here means that there is no DHCP server on this network.
The wireless Ethernet or wlo1 was assigned 192.168.11.50/24. 192.168.*.* means “inside only” or private IP address space. And 192.168.11.0/24 means a chunk within that.
To put it another way, this means that:
127.*.*.* = “localhost”, communication within this one computer only
169.254.*.* = “AutoConf”, automatic configuration, called Bonjour or often known as Rendezvous among other names by Apple. Communication within the LAN, and there is no functioning DHCP server.
“Link-only” or “inside-only” addresses are private IP address spaces that can be written in three equivalent ways:
10/8
10.0.0.0/8
10.*.*.*
172.16/12
172.16.0.0/12
172.16.*.* – 172.31.*.*
192.168/16
192.168.0.0/16
192.168.*.*
To communicate with external servers, you will need a NAT router, or a proxy gateway doing NAT. And because CompTIA is fussy about terms, it’s actually NAT/PAT for what you’re used to.
IPv6
These addresses are 128 bits long, which are represented in base 16 or hexadecimal, 0-9 plus a-f, with colons between 16-bit or 4-character chunks which may be compressed together. You don’t need to know much aside from:
::1 or ::1/128 = localhost in IPv6
fe80::/64 = link-local-only IPv6, on the local LAN but not routable to the world outside.
Read more >> CompTIA order of volatility
ping
Recognize errors. We are directly connected and plugged into the same switch in the following. Our host, 192.168.11.12, is reporting that 192.168.11.88, our target, is unreachable. It recognizes that the target is on the same LAN, therefore it should be able to find the target hardware address using ARP, but it can’t.
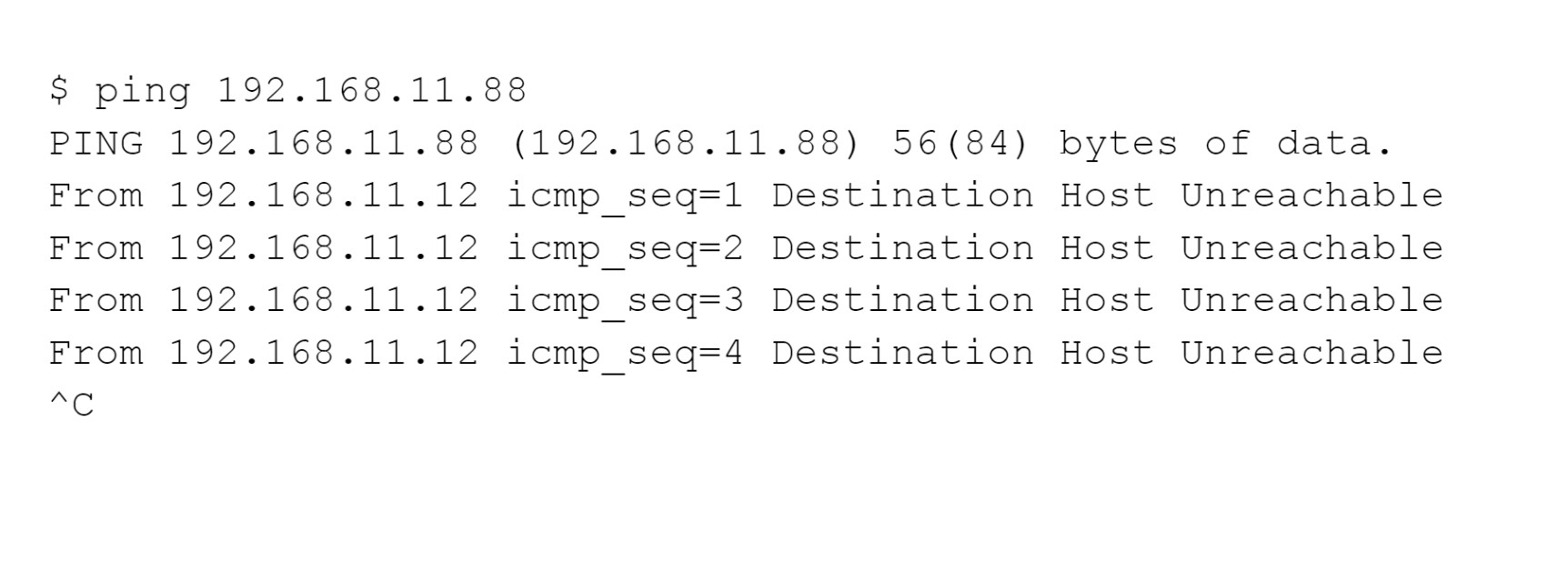
The host is a few router hops away and it isn’t responding, nothing came back in the following. You might see that some router between here and there reporting that it’s unreachable. And it’s a silent failure here.
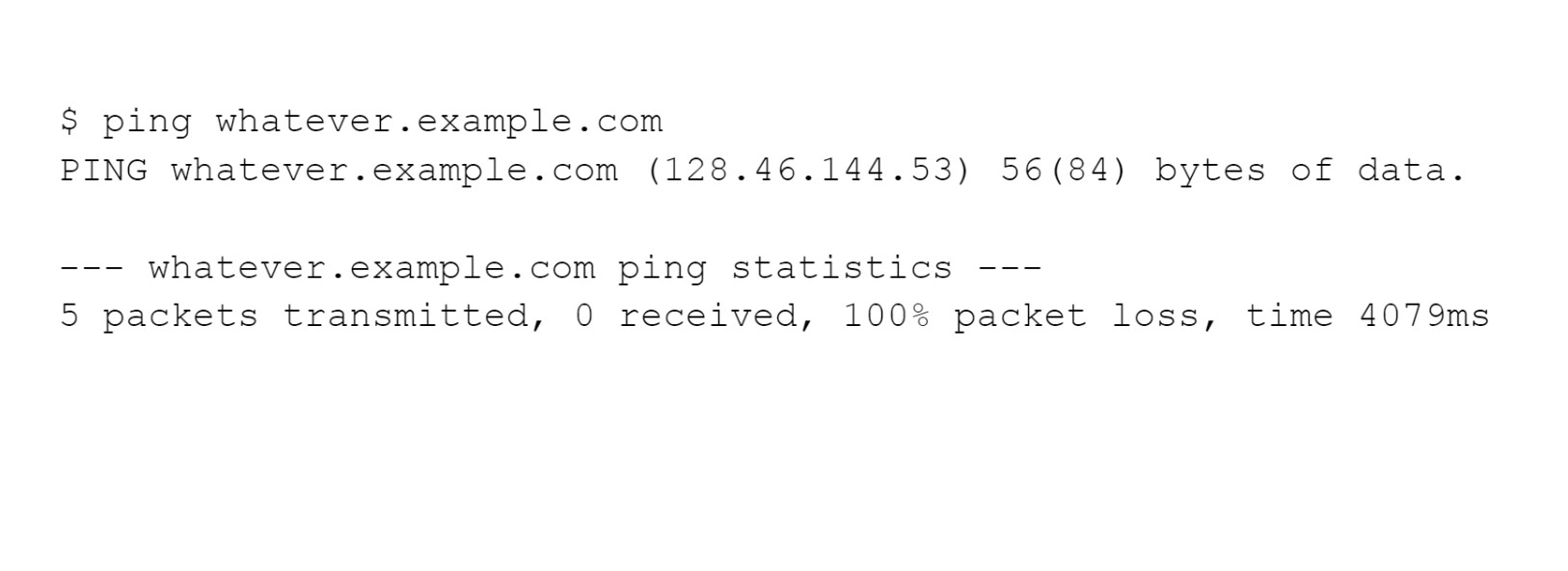
We asked for a name that does not exist in the following. Either we misspelled it or there isn’t a record for it on the relevant DNS server.
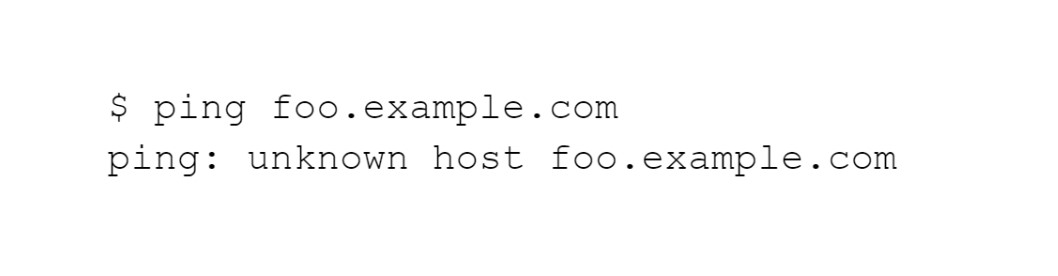
We may see another form the above error may take in this last one.
traceroute
On Windows, it’s spelled tracert. Recognize DNS errors as shown above.
The output will look somewhat like this, with one line per router and three probes per router along the way. Line 1 is hop #1, line 2 is the router 2 hops away, and etc.
You’ll see “*” instead of a time if you don’t get a response within the timeout period. The router at that distance didn’t respond at all, as indicated by a line with three stars. It responded some and timed out some if you see its names or IP addresses and then a mix of times and stars.
An unending series of probes that timed out indicates that it either reached the target and the target did not respond (very common for web servers) or that the network is broken beyond the last router that responded.
Finally, slightly inconsistent DNS configurations may add to the confusion.
For example, you’re in a hostel in Fukuoka, Japan, and you’ve requested a trace to the Purdue Federal Credit Union in West Lafayette, Indiana, United States. You specifically requested that the IP addresses be converted to fully qualified domain names. Depending on your tool’s version, it may only provide IP addresses by default.
This example shows some of the DNS oddities that could occur. The name www.purduefed.com is an alias; the canonical name is purduefed.com. Then, the hosting company hasn’t changed the PTR record mapping from IP address to name. It used to do business as Purdue Employees Federal Credit Union, and it used the domain purdueefcu.com, which appears as the last hop. For that IP address, there was an outdated PTR record.
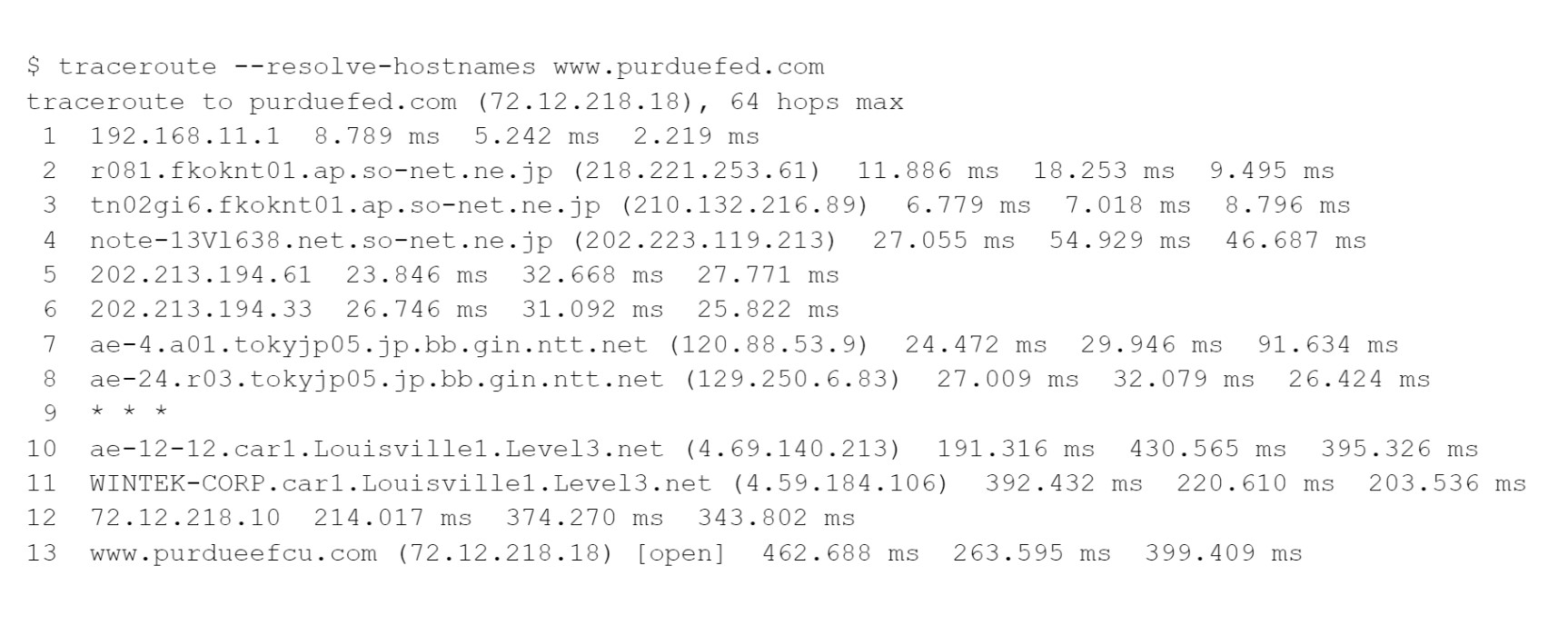
Hop #1 is the hostel’s wireless access point. 192.168.0.0/16 is a private block of IP addresses that is commonly used by small routers.
Hops #2-4 are across the so-net.ne.jp network in Japan.
Hops #5 and hops 6 are routers in the 202.213.194.0/24 network. So-net.ne.jp owns that network as well, but they’ve not set up DNS pointer records, so we just see IP addresses rather than names. This could be regarded as an error caused by a lack of DNS data. It’s basically only a problem for easily interpreting traceroute output, so you would only select it as an error if there was nothing else.
Hops #7 and hops 8 are across ntt.net, a major network provider in Japan.
Hop #9 was timed out all three times. The timed-out packets were dropped by that router, but no ICMP error reports were returned. Later steps returned results, indicating that this router was not responding as expected, despite the fact that it was able to successfully forward packets for the later steps. Again, you may not see this as an error, but if you had to choose something, this seems to you that this is a better choice than the lack of DNS pointer records for hops 5-6.
Hops #10 and hop 11 are across level3.net routers, a major worldwide provider. The round-trip times generally increase but look at how much larger hop #10 they are. The router at hop #8 was in Japan, then hop #10 was in the United States.
Hop #12 is another router whose name doesn’t resolve. Wintek, a network provider in Lafayette, Indiana, owns the 72.12.192.0/192 range (that is, 72.12.192.0 through 72.12.223.255).
Hop #13 is the final stop.
All the individual packets returned ICMP reports other than the three sent to hop #9. When just one or two packets time out, you will see “*” instead of a time.
You may notice that each packet is routed individually. The three packets sent with a given TTL may take various routes, resulting in two or three hostnames or IP addresses being reported on the line.
Read more >> How long to study for Security+
netstat
Depending on the command-line option, the netstat command can display a variety of things. Ethernet interface statistics with -i, routing table with -r, and so on.
The -a option asks for the state of all services, and -n implies don’t try to map back to host names using DNS. Here’s an example:
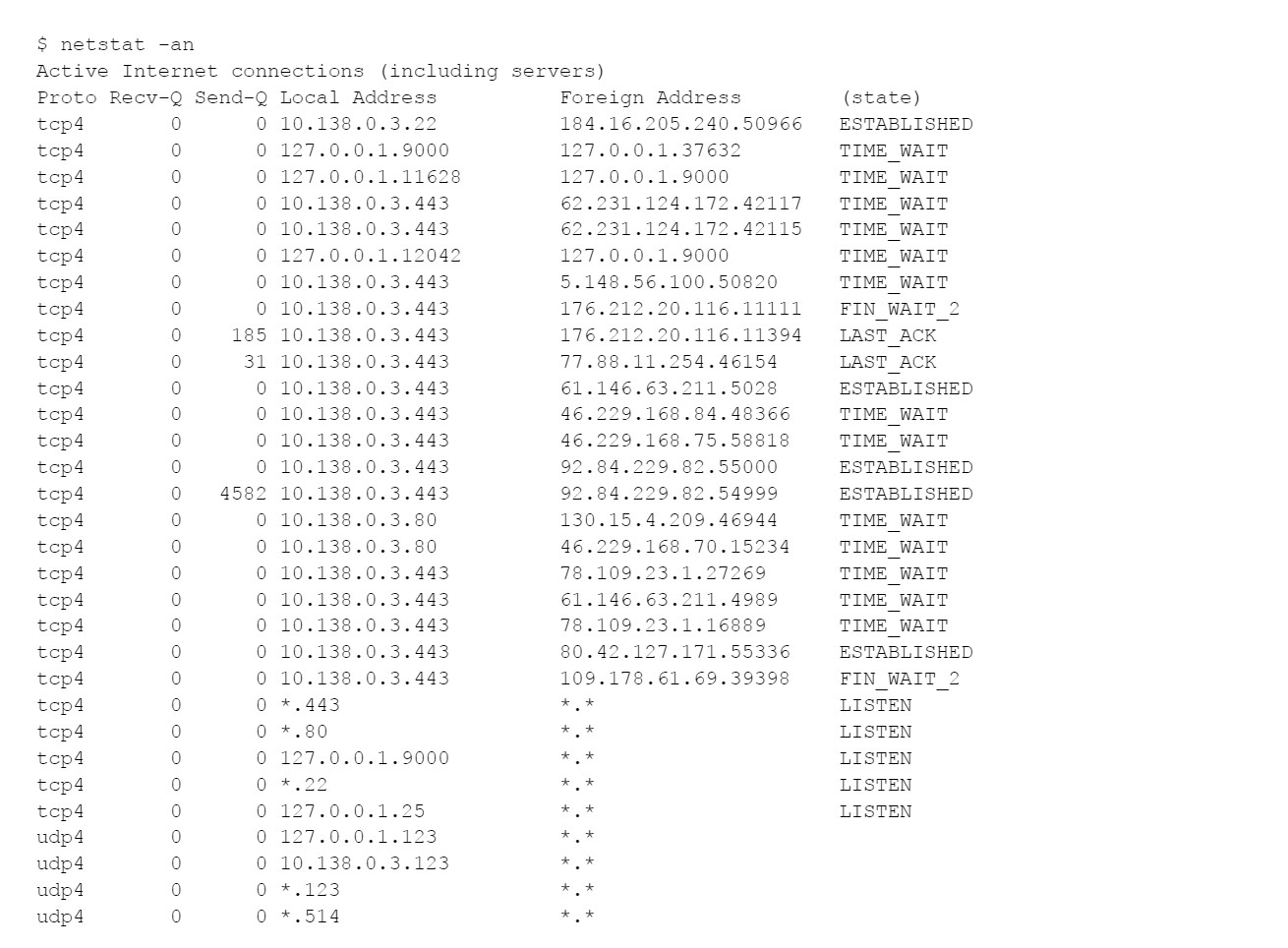
“LISTEN” means that a service process is listening for connections. “ESTABLISHED” indicates that a client is currently connected and transferring data. Others TCP states including “TIME_WAIT”, “LAST_ACK”, “FIN_WAIT”, “FIN_WAIT_2”, and others, mean that we caught a connection in the process of being established or shut down.
SSH is listening for new connections on TCP/22, and an SSH connection is currently established, as shown above, connected in from 184.16.205.240, running the netstat command.
My server accepts HTTP (TCP/80) connections and promptly redirects clients to the same URL over HTTPS (TCP/443). That is called HTTPS redirect, and it’s a security best practice that you’ll need to know on the test.
Conclusion
Those who want to take the CompTIA Security+ SY0-601 exam should pay special attention to the exam objectives and understand each of the points listed under each domain. There is a lot of work to be done, and perhaps this article has assisted you in learning commands to know for Security+.

PCCN vs CCRN: Which Certification Should I Take?
In this discussion, we will examine the fundamental distinctions between PCCN vs CCRN certifications, allowing you to make an informed and right decision about which certification is best for your nursing career progression.
June 20, 2023

Is PCCN Worth It? A Comprehensive 2025 Study Guide
In this article, we will provide all the enrollment criteria, how to apply, whether is PCCN worth it for you to obtain, and how to get a high mark.
June 20, 2023

PCCN Requirements - How to Become a Progressive Care Certified Nurse?
To become a progressive care nurse, you must first obtain the PCCN certification. This post will help you understand PCCN certification, PCCN requirements, and efficient approaches to obtaining this certification.
June 20, 2023

